 Diagram of GOST | |
| General | |
|---|---|
| Designers | USSR, KGB, 8th Department |
| First published | 1994-05-23 (declassified) |
| Successors | GOST hash function, Kuznyechik |
| Certification | GOST standard |
| Cipher detail | |
| Key sizes | 256 bits |
| Block sizes | 64 bits |
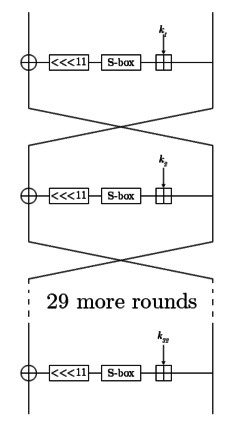
| Structure | Feistel network |
| Rounds | 32 |
| Best public cryptanalysis | |
| In 2011 several authors discovered more significant flaws in GOST, being able to attack the full 32-round GOST with arbitrary keys for the first time. It has even been called "a deeply flawed cipher" by Nicolas Courtois.[1] | |
The GOST block cipher (Magma), defined in the standard GOST 28147-89 (RFC 5830), is a Soviet and Russian government standard symmetric key block cipher with a block size of 64 bits. The original standard, published in 1989, did not give the cipher any name, but the most recent revision of the standard, GOST R 34.12-2015 (RFC 7801, RFC 8891), specifies that it may be referred to as Magma.[2] The GOST hash function is based on this cipher. The new standard also specifies a new 128-bit block cipher called Kuznyechik.
Developed in the 1970s, the standard had been marked "Top Secret" and then downgraded to "Secret" in 1990. Shortly after the dissolution of the USSR, it was declassified and it was released to the public in 1994. GOST 28147 was a Soviet alternative to the United States standard algorithm, DES.[3] Thus, the two are very similar in structure.
- ^
Courtois, Nicolas T. (9 May 2011). "Security Evaluation of GOST 28147-89 In View Of International Standardisation". Cryptology ePrint Archive. IACR.
Until 2011 researchers unanimously agreed that GOST could or should be very secure, which was summarised in 2010 in these words: despite considerable cryptanalytic efforts spent in the past 20 years, GOST is still not broken". Unhappily, it was recently discovered that GOST can be broken and is a deeply flawed cipher
- ^ Cite error: The named reference
std2015was invoked but never defined (see the help page). - ^ Fleischmann, Ewan; Gorski, Michael; Hühne, Jan-Hendrik; Lucks, Stefan (2009). "Key Recovery Attack on Full GOST Block Cipher with Zero Time and Memory". Published as ISO/IEC JTC. 1.