This article includes a list of general references, but it lacks sufficient corresponding inline citations. (July 2013) |
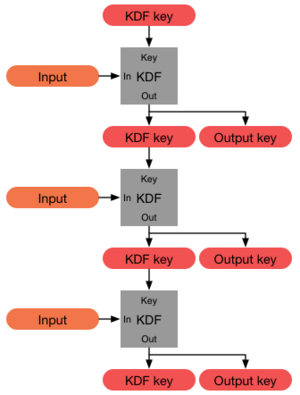
In cryptography, a key derivation function (KDF) is a cryptographic algorithm that derives one or more secret keys from a secret value such as a master key, a password, or a passphrase using a pseudorandom function (which typically uses a cryptographic hash function or block cipher).[1][2][3] KDFs can be used to stretch keys into longer keys or to obtain keys of a required format, such as converting a group element that is the result of a Diffie–Hellman key exchange into a symmetric key for use with AES. Keyed cryptographic hash functions are popular examples of pseudorandom functions used for key derivation.[4]
- ^ Bezzi, Michele; et al. (2011). "Data privacy". In Camenisch, Jan; et al. (eds.). Privacy and Identity Management for Life. Springer. pp. 185–186. ISBN 9783642203176.
- ^ B. Kaliski; A. Rusch (January 2017). K. Moriarty (ed.). PKCS #5: Password-Based Cryptography Specification Version 2.1. Internet Engineering Task Force (IETF). doi:10.17487/RFC8018. ISSN 2070-1721. RFC 8018. Informational. Obsoletes RFC 2898. Updated by RFC 9579.
- ^ Chen, Lily (October 2009). "NIST SP 800-108: Recommendation for Key Derivation Using Pseudorandom Functions". NIST.
- ^ Zdziarski, Jonathan (2012). Hacking and Securing IOS Applications: Stealing Data, Hijacking Software, and How to Prevent It. O'Reilly Media. pp. 252–253. ISBN 9781449318741.